By Divya Roopam
Cryptosystems
A cryptographic system is any computer system that involves cryptography. Such systems include for instance, a system for secure electronic mail which might include methods for digital signatures, cryptographic hash functions, key management techniques, and so on. Cryptographic systems are made up of cryptographic primitives, and are usually rather complex. Because of this, breaking a cryptosystem is not restricted to breaking the underlying cryptographic algorithms - usually it is far easier to break the system as a whole, e.g., through the not uncommon misconceptions of users in respect to the cryptosystem. The systematic arrangement of cypher text can abide the security.
In the context of cryptography, a cryptosystem refers to a suite of algorithms needed to implement a particular form of encryption and decryption.
By definition, a cryptosystem is the combination of three elements: an encryption engine, keying information, and operational procedures for their secure use. The term cipher is often used to refer to a pair of algorithms, one for encryption and one for decryption. Therefore, the term "cryptosystem" is most often used when the key generation algorithm is important.
To secure high-value data on a hard disk (or on back-up media), it is necessary to employ a high-grade cryptosystem: one which even an attacker possessing both a copy of your encryption engine and knowledge of your operating procedures cannot break without your keying information.
A low-grade cryptosystem is one which an attacker can break by means of purely cryptanalytic attacks on the ciphertext it produces, but which may delay him long enough for the period of time during which the corresponding plaintext that it encrypted has value.
A medium-grade cryptosystem is one which cannot be broken in a useful time without the attacker possessing a copy of the encryption engine, which he can use in chosen plaintext attacks to help recover your key.
High-grade encryption has no "short cuts" to breaking it with less expense than would be required to repeatedly try decryption with different key values until one works. Its strength hinges on the degree to which an attacker cannot predict that certain values are more probable than others through knowledge of the key generation process.
There are three types of Cryptosystems: Symmetric key, Asymmetric key and Hash Functions.
Symmetric key encryption uses one key to encrypt and decrypt. Asymmetric key encryption uses two keys; when one key is used to encrypt, the other is used to decrypt. Hash functions create a message digest via an algorithm and use no key.
Symmetric key cryptosystem: Symmetric key (also called private key or secret key) cryptography uses the same key to encrypt and decrypt. The name “private key” derives from the need to keep the key private. A major challenge associated with symmetric key cryptosystems is the secure distribution of keys.
Common symmetric key encryption algorithms include DES (the Data Encryption Standard) and AES (the Advanced Encryption Standard).
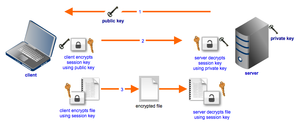
Asymmetric Key Encryption: Asymmetric key encryption (also called public key encryption) uses two keys: a public and a private key. Data encrypted with one key can be decrypted only with the other key.
In summary, Symmetric key and Asymmetric key encryption provide confidentiality, which ensures the privacy of data. They can also be used to provide authentication (where knowledge of a key serves as proof of identity). Hash functions can be used to provide integrity, which ensures that data has not been altered. Additionally, Asymmetric key encryption (often combined with hashes) can be used for non-repudiation (proving a user performed a specific action).
In the context of cryptography, a cryptosystem refers to a suite of algorithms needed to implement a particular form of encryption and decryption.
By definition, a cryptosystem is the combination of three elements: an encryption engine, keying information, and operational procedures for their secure use. The term cipher is often used to refer to a pair of algorithms, one for encryption and one for decryption. Therefore, the term "cryptosystem" is most often used when the key generation algorithm is important.
To secure high-value data on a hard disk (or on back-up media), it is necessary to employ a high-grade cryptosystem: one which even an attacker possessing both a copy of your encryption engine and knowledge of your operating procedures cannot break without your keying information.
A low-grade cryptosystem is one which an attacker can break by means of purely cryptanalytic attacks on the ciphertext it produces, but which may delay him long enough for the period of time during which the corresponding plaintext that it encrypted has value.
A medium-grade cryptosystem is one which cannot be broken in a useful time without the attacker possessing a copy of the encryption engine, which he can use in chosen plaintext attacks to help recover your key.
High-grade encryption has no "short cuts" to breaking it with less expense than would be required to repeatedly try decryption with different key values until one works. Its strength hinges on the degree to which an attacker cannot predict that certain values are more probable than others through knowledge of the key generation process.
There are three types of Cryptosystems: Symmetric key, Asymmetric key and Hash Functions.
Symmetric key encryption uses one key to encrypt and decrypt. Asymmetric key encryption uses two keys; when one key is used to encrypt, the other is used to decrypt. Hash functions create a message digest via an algorithm and use no key.
Symmetric key cryptosystem: Symmetric key (also called private key or secret key) cryptography uses the same key to encrypt and decrypt. The name “private key” derives from the need to keep the key private. A major challenge associated with symmetric key cryptosystems is the secure distribution of keys.
Common symmetric key encryption algorithms include DES (the Data Encryption Standard) and AES (the Advanced Encryption Standard).
Asymmetric Key Encryption: Asymmetric key encryption (also called public key encryption) uses two keys: a public and a private key. Data encrypted with one key can be decrypted only with the other key.
In summary, Symmetric key and Asymmetric key encryption provide confidentiality, which ensures the privacy of data. They can also be used to provide authentication (where knowledge of a key serves as proof of identity). Hash functions can be used to provide integrity, which ensures that data has not been altered. Additionally, Asymmetric key encryption (often combined with hashes) can be used for non-repudiation (proving a user performed a specific action).