By Priyanshi Goyal
From Prehistory to Modern era
It seems reasonable to assume that people have tried to conceal information in written form since writing was developed and examples survive in stone inscriptions and papyruses showing that many ancient civilisations including the Egyptians, Hebrews and Assyrians all developed cryptographic systems.
Few are the crypting techniques used in the ancient times:
It seems reasonable to assume that people have tried to conceal information in written form since writing was developed and examples survive in stone inscriptions and papyruses showing that many ancient civilisations including the Egyptians, Hebrews and Assyrians all developed cryptographic systems.
Few are the crypting techniques used in the ancient times:
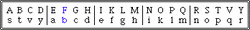
Caesar's Cipher
Caesar’s Cipher
Julius Caesar invented the first substitution cipher, which bears his name to this day. The substitution key is formed by cyclically displacing an alphabet with respect to itself. A message, called "plaintext", is enciphered by substituting for each letter the corresponding letter from the shifted alphabet. The substitution produces a new string of letters called "cipher text". A cryptogram enciphered in this way can be deciphered by reversing the process and translating each cipher text letter into its plaintext equivalent.
Julius Caesar invented the first substitution cipher, which bears his name to this day. The substitution key is formed by cyclically displacing an alphabet with respect to itself. A message, called "plaintext", is enciphered by substituting for each letter the corresponding letter from the shifted alphabet. The substitution produces a new string of letters called "cipher text". A cryptogram enciphered in this way can be deciphered by reversing the process and translating each cipher text letter into its plaintext equivalent.

Scytale
Scytale (Transposition Cipher)
As early as the fifth century B.C., the Spartans employed a device called the 'scytale' which consists of a baton of wood around which a strip of papyrus or leather or parchment is wrapped close-packed. The secret message is written on the parchment down the length of the baton; the parchment is then unwound and sent on its way.
Once unwrapped the parchment appeared to contain an incomprehensible set of letters, however when wrapped around another baton of identical size the original text appears.
As early as the fifth century B.C., the Spartans employed a device called the 'scytale' which consists of a baton of wood around which a strip of papyrus or leather or parchment is wrapped close-packed. The secret message is written on the parchment down the length of the baton; the parchment is then unwound and sent on its way.
Once unwrapped the parchment appeared to contain an incomprehensible set of letters, however when wrapped around another baton of identical size the original text appears.
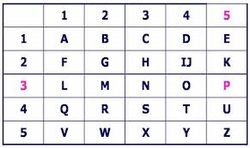
Polybius Checkerboard
Polybius Checkerboard
Originally conceived by the Greek historian Polybius in the second century B.C., the Polybius square or Polybius checkerboard is one of the simplest tools in cryptography. You can use a Polybius square to encode a message that can then be deciphered only by someone who knows the arrangement of letters in the square.
Originally conceived by the Greek historian Polybius in the second century B.C., the Polybius square or Polybius checkerboard is one of the simplest tools in cryptography. You can use a Polybius square to encode a message that can then be deciphered only by someone who knows the arrangement of letters in the square.
Pre-War Era
By 1860 large codes were in common use for diplomatic communications and cipher systems had become a rarity for this application however cipher systems prevailed for military communications (except for high-command communications because of the difficulty of protecting codebooks from capture or compromise). During the US Civil War the Federal Army extensively used transposition ciphers. The Confederate Army primarily used the Vigenère cipher and on occasional monoalphabetic substitution. While the Union cryptanalysts solved most of the intercepted Confederate ciphers, the Confederacy in desperation, sometimes published Union ciphers in newspapers, appealing for help from readers in cryptanalysing them.
The Two World Wars: The advent of Telegraph
In the middle of the nineteenth century, the telegraph generated a new craze for cryptography and cryptanalysis. Kasiski in 1863 gave a method to attack polyalphabetical substitutions. Mathematics are introduced in cryptology, and Kerckhoffs gave a few laws that should be verified by a ``good'' cryptographic system. In particular he insists on the fact that the system has to be public, the only secret being a key.
During the first world war both sides employed cipher systems almost exclusively for tactical communications while code systems were still used mainly for high-command and diplomatic communications. Although field cipher systems such as the U.S. Signal Corps cipher disk lacked sophistication, some complicated cipher systems were used for high-level communications by the end of the war. The most famous of these was the German ADFGVX fractionation cipher.
The last fifty years
The key facts of the last years are the increasing development of computers, and the great interest of civilians for cryptography.
In the beginning of the 70's, the National Bureau of Standards decided to publish a cryptosystem which could be used by governmental agencies or banks; this was done in 1977, with the Data Encryption Standard (DES). Concurrently to this, Diffie invented in 1975 the concept of public-key cryptosystem, which was applied by Rivest, Shamir and Adleman (RSA) in 1977.
There is now a great link between cryptology and some branches of modern mathematics and computer science: probability theory, information theory, algorithmic number theory, or the theory of error correcting codes are useful tools.
Nowadays, some new applications of cryptography appear: electronic trade, money, or notarial deeds.
By 1860 large codes were in common use for diplomatic communications and cipher systems had become a rarity for this application however cipher systems prevailed for military communications (except for high-command communications because of the difficulty of protecting codebooks from capture or compromise). During the US Civil War the Federal Army extensively used transposition ciphers. The Confederate Army primarily used the Vigenère cipher and on occasional monoalphabetic substitution. While the Union cryptanalysts solved most of the intercepted Confederate ciphers, the Confederacy in desperation, sometimes published Union ciphers in newspapers, appealing for help from readers in cryptanalysing them.
The Two World Wars: The advent of Telegraph
In the middle of the nineteenth century, the telegraph generated a new craze for cryptography and cryptanalysis. Kasiski in 1863 gave a method to attack polyalphabetical substitutions. Mathematics are introduced in cryptology, and Kerckhoffs gave a few laws that should be verified by a ``good'' cryptographic system. In particular he insists on the fact that the system has to be public, the only secret being a key.
During the first world war both sides employed cipher systems almost exclusively for tactical communications while code systems were still used mainly for high-command and diplomatic communications. Although field cipher systems such as the U.S. Signal Corps cipher disk lacked sophistication, some complicated cipher systems were used for high-level communications by the end of the war. The most famous of these was the German ADFGVX fractionation cipher.
The last fifty years
The key facts of the last years are the increasing development of computers, and the great interest of civilians for cryptography.
In the beginning of the 70's, the National Bureau of Standards decided to publish a cryptosystem which could be used by governmental agencies or banks; this was done in 1977, with the Data Encryption Standard (DES). Concurrently to this, Diffie invented in 1975 the concept of public-key cryptosystem, which was applied by Rivest, Shamir and Adleman (RSA) in 1977.
There is now a great link between cryptology and some branches of modern mathematics and computer science: probability theory, information theory, algorithmic number theory, or the theory of error correcting codes are useful tools.
Nowadays, some new applications of cryptography appear: electronic trade, money, or notarial deeds.
 RSS Feed
RSS Feed